AI Agents & Cybersecurity: Lessons from Building AI-Powered Workflows with N8N
In recent years, we’ve seen the letters ‘AI’ appear almost everywhere, driven by the rise of large language models (LLMs). More recently, the concept of "AI agents", AI-powered automation capable of making decisions and taking actions, has gained significant traction.
As someone who enjoys exploring new technologies, I stumbled upon N8N during a geeky conversation about home labs with a colleague (more on that in a future post). For those unfamiliar, N8N is a workflow automation tool that enables low-code automation across various services. Unlike many commercial automation tools, N8N offers a self-hosted option for free, making it particularly appealing to developers and businesses wanting full control over their data.
Having experience with Azure Logic Apps, With the support of Youtube resources (linked at the bottom) I found the learning curve relatively smooth. I deployed N8N via Docker, set up a few simple workflows, and before long, I found myself deep down the AI agents rabbit hole, spurred on by YouTube tutorials on integrating AI tools. Intrigued by the possibilities, I purchased $10 in OpenAI credits and began experimenting with building my own AI-powered personal assistant.
Building AI-Powered Workflows in N8N
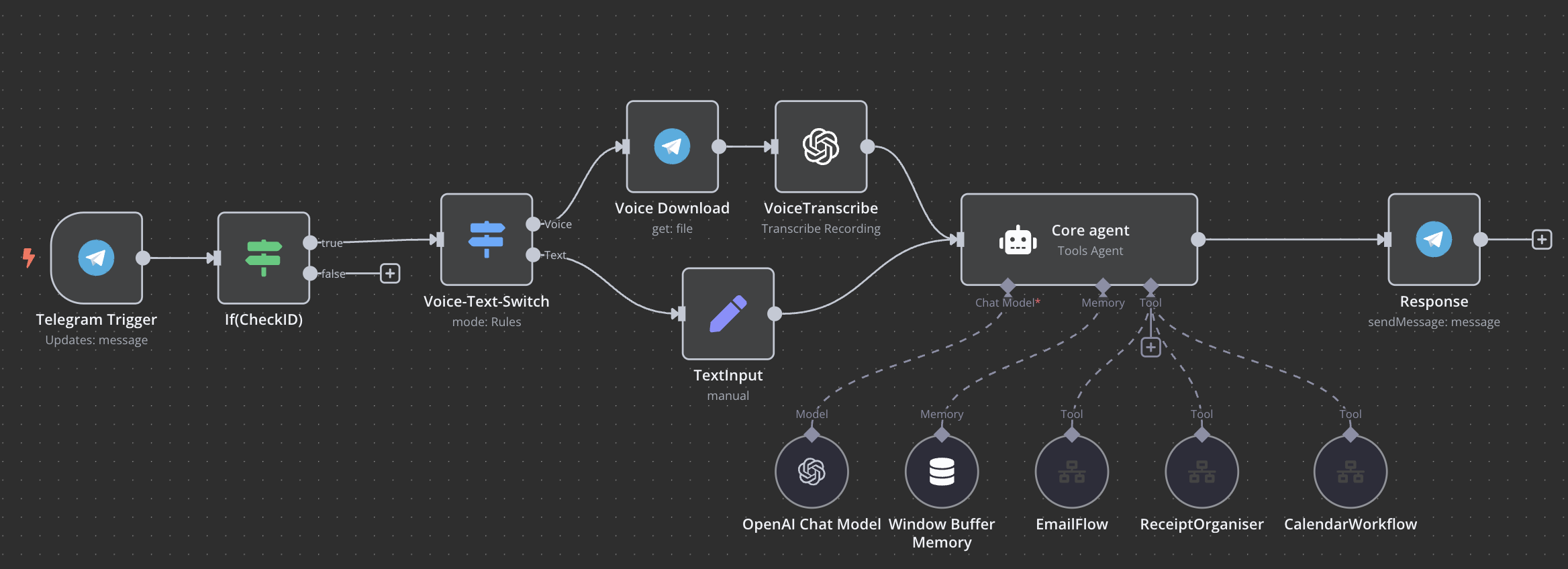
One of my first AI-driven workflows involved integrating Telegram as an input trigger, allowing me to send voice or text commands. The AI agent would then process these commands and interact with various services, such as:
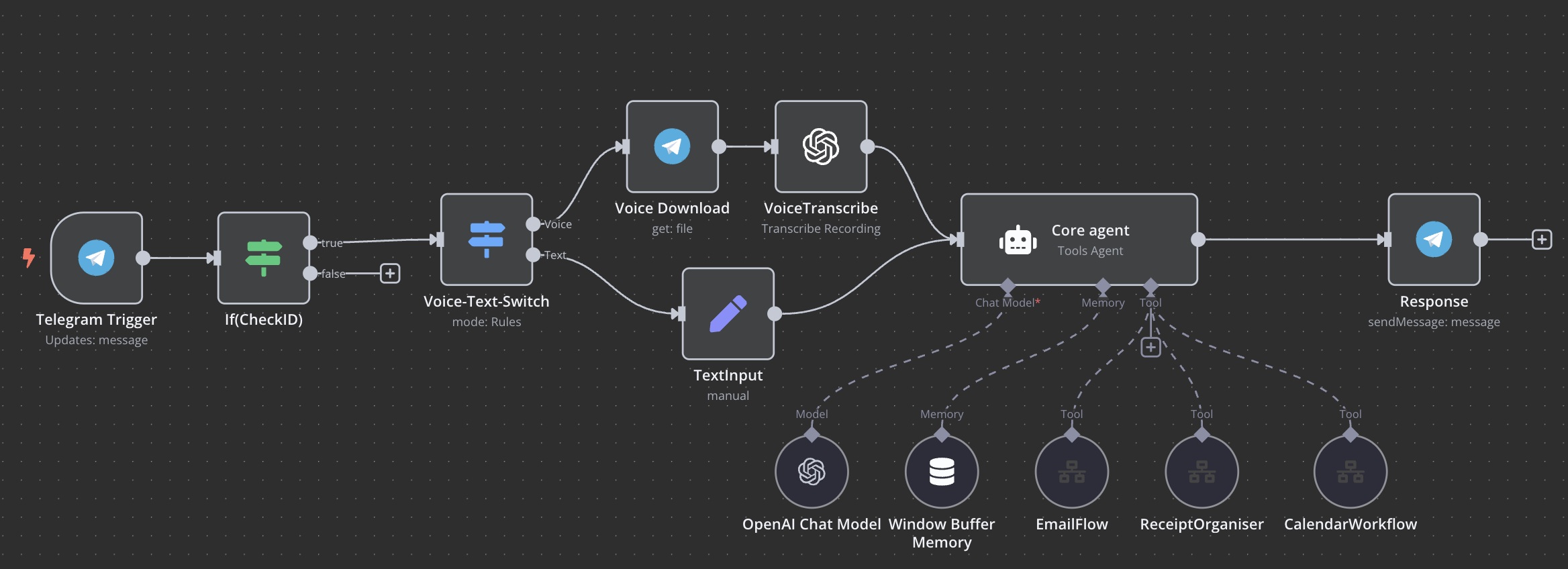
- Google Calendar – Adding or modifying events.
- Gmail/Outlook – Summarising emails or sending messages.
Other workflows I’ve built include:
- Morning Brief – Inspired by Samsung’s ‘Now Brief,’ this workflow analyses emails, to-do lists, and calendar events each morning to generate a summary of the most important tasks.
- Receipt Scanner – When I forward an image of a receipt to a shared mailbox, the workflow extracts relevant data, saves the receipt in a specific folder, and logs the details in Google Sheets.
Cybersecurity Challenges
As someone with a cybersecurity background, I wanted to assess the risks of AI-powered automation. Unlike traditional chatbots, AI agents have direct access to data and services, making them vulnerable to both LLM-specific threats (e.g., prompt injection) and automation security risks.
Common Cyber Security Risks & Mitigations
(Note: This is not an exhaustive list of risks, but it highlights some of the security considerations when using AI-powered workflows.)
1. Unauthorised Access to AI Interfaces
Many AI agent workflows use external messaging platforms (e.g., Telegram) as input triggers, which can expose them to unauthorised prompts. Some YouTube guides overlook a major issue: anyone who finds your Telegram bot can send arbitrary commands to it.
🔴 Potential Risks:
- Data leakage – “What’s in my calendar today?”
- Unauthorised actions – “Send an email to X requesting a transfer.”
- Smart home exploitation – If workflows interact with IoT devices, attackers could manipulate them (e.g., unlocking doors).
✅ Mitigation Strategies:
- Restrict bot interactions to approved users only e.g. Telegram whitelisting in my flow you can see an 'IF' statement which only continues the workflow if it is initiated from an approved chatID. I am still looking at better ways to approach this as a large number of requests can overwhelm resources.
- Use authentication tokens for webhook security.
2. Security of Self-Hosted N8N Deployments
While self-hosting N8N provides greater control, it also means securing the infrastructure falls entirely on you. If compromised, an attacker could gain access to all connected services (email, cloud storage, APIs, etc.), making it a high-value target.
✅ Mitigation Strategies:
- Follow the principle of least privilege:
- If an email integration only needs read access, don’t grant write access.
- Disable public API access if not needed to reduce attack surface.
- Restrict node permissions based on role-based access control (RBAC).
- Network security:
- Run N8N behind a reverse proxy and/or integrate with your IdP. e.g. Using Entra conditional access policies to only allow access from compliant devices/networks.
- Use TLS encryption for all communication.
- Logging & monitoring:
- Enable audit logs to track workflow execution.
- Set up alerts for unauthorised API calls.
API Security & Webhook Protection
Since N8N integrates multiple services via APIs and webhooks, attackers could exploit misconfigured endpoints to manipulate workflows.
🔴 Potential Risks:
- Webhook enumeration – Attackers discover and abuse open webhook endpoints.
- API key leakage – If stored insecurely, API keys can be extracted and misused.
✅ Mitigation Strategies:
- Use webhook authentication (e.g. signed requests, JWT tokens).
- Rotate API keys and avoid hardcoding credentials in workflows.
Account Security & Access Controls
To prevent unauthorised access to the N8N instance itself, strong authentication mechanisms should be enforced.
✅ Mitigation Strategies:
- SSO Integration (Enterprise Only) – Use Entra ID (Azure AD) for authentication and enforce Conditional Access policies.
- Multi-Factor Authentication (MFA) – If SSO is unavailable, enable MFA for additional security.
- Avoid self-hosting if lacking expertise – While self-hosting grants full control, it requires ongoing security management and the cost vs risk must be considered
Final Thoughts
AI-powered workflows offer exciting automation possibilities, but security cannot be an afterthought. Whether you're self-hosting or using a managed service, a secure by design approach must be adopted. This includes securing inputs, enforcing authentication, limiting permissions, and regularly reviewing workflow access.
My N8N journey is still new, I’ll continue exploring and —stay tuned for future updates!
If you have any questions, comments, or suggestions for amendments, please leave a comment on this page (members only) or reach out to me via one of the links on my Contact Page.
A few resources I have used to learn about N8N Agent related workflows: