An Introduction to Cybersecurity in SATCOM: Threats, Defences, and Future Challenges
Satellite communication powers navigation, internet, broadcasting, and critical infrastructure. As Starlink and mega-constellations grow, the attack surface expands. This post introduces SATCOM security threats, defenses, and future challenges.

Towards the end of 2024, I was in Orlando and had the chance to watch a SpaceX launch from a distance. Most people probably see a rocket launch as a spectacle of science and engineering, but what was in the back of my mind was the sheer importance of the satellites being placed into orbit, and how they could be attacked. They underpin so much of modern life: from the GPS we casually use to navigate in our cars, to enabling global business, powering scientific discovery, and serving as critical infrastructure for military operations.
With the rapid rise of consumer-focused satellite services, this importance is only going to increase. As satellites become more tightly woven into our daily lives, providing internet connectivity, navigation, and personal communications, they will also become more attractive targets. Today, most attacks against satellites are driven by nation-states, intent on disrupting military communications or eavesdropping on sensitive data. But looking ahead, the threat surface is widening. Cybercriminals and other non-state actors will likely see commercial and consumer satellite services as valuable targets, creating new security challenges that extend far beyond the traditional state-on-state domain.
Before going further, I should caveat that this post is very much a learning exercise for me. My aim is to share what I’ve discovered so far, but also (perhaps slightly selfishly) to use writing as a way to solidify my own understanding. I’d welcome any challenges, corrections, or additions from readers to help close gaps in my learning.
Introduction to Satellite Communications (SATCOM)
For those of you that are like me and new to SATCOM this section introduces some key concepts around architecture and communications communications.
Core Components
When we talk around SATCOM we're really describing a system made up of three main components:
- Space Segment - These are the satellites themselves, orbiting earth and carrying the payloads (transponders, sensors, antennas) that make communication possible.
- Ground Segments - These are the ground stations that control satellites, route signals and connect them to terrestrial networks.
- User Segment: The end devices people use such as GPS receivers in our cars to dishes for Sky TV or Broadband services like Starlink.
Orbits: LEO, MEO, GEO
Satellites can orbit Earth at different altitudes, each with trade-offs:
- Low Earth Orbit (LEO): ~500-1200km above Earth. Constellations like Starlink use thousands of LEO satellites to deliver low-latency internet worldwide. Common use cases include imaging, IoT and real-time communications but coverage requires many satellites.
- Medium Earth Orbit (MEO): ~2,000–20,000 km. Often used for navigation systems like GPS, Galileo, and GLONASS. Balances coverage and latency.
- Geostationary Orbit (GEO): ~36,000 km. A satellite here appears “fixed” in the sky because it rotates with Earth’s equatorial angle. Perfect for TV broadcasting (e.g., Sky TV) and weather monitoring, but has higher latency due to distance.
Orbital Geometry & Rotation
A satellite’s orbit isn’t just about how high it is above Earth (LEO, MEO, GEO). Its geometry (shape, angle, and direction of travel) determines what part of the Earth it can see, how often it passes over, and what it can be used for. Orbital geometry drives coverage, latency and resilience.
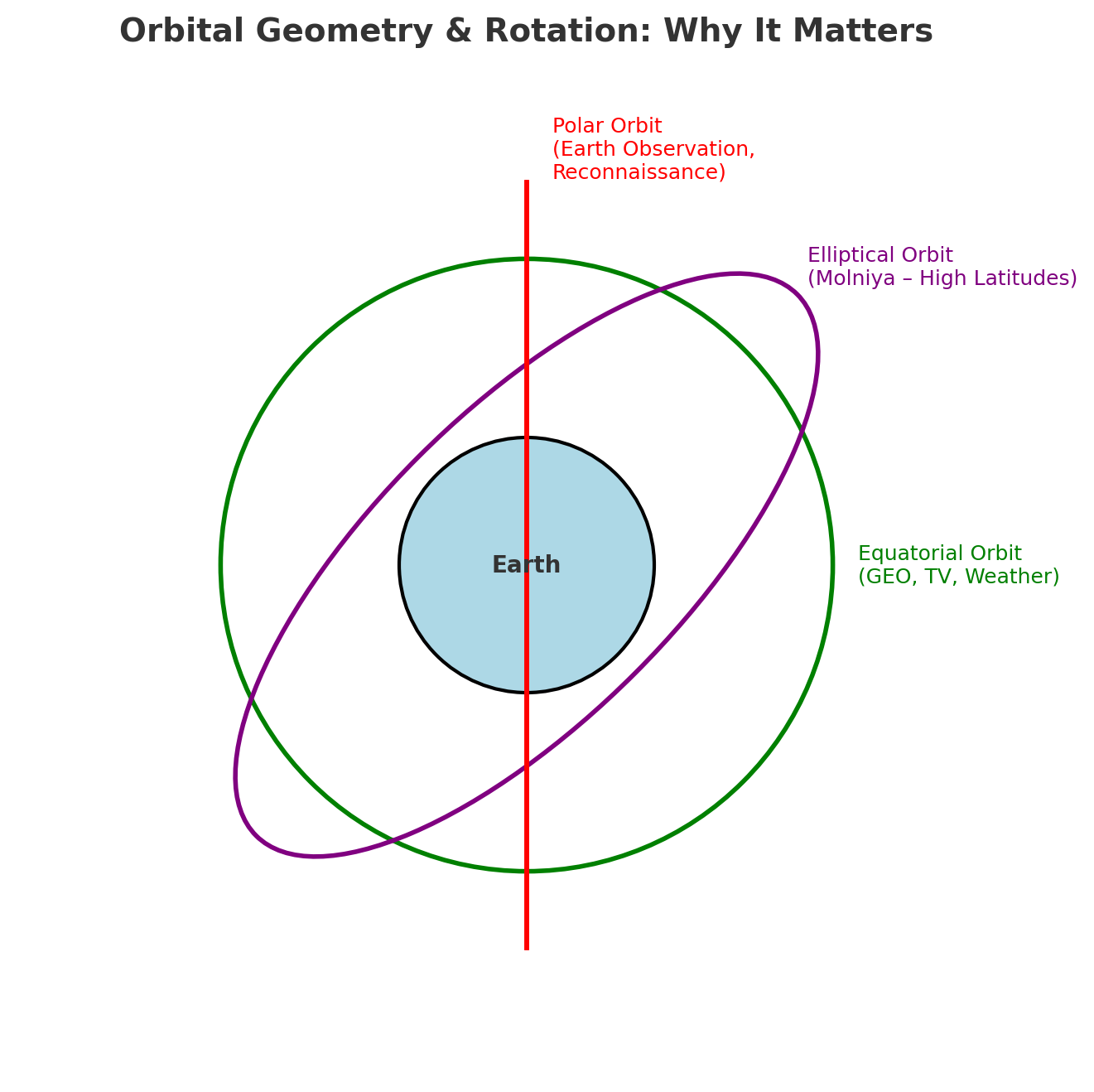
- Orbital Shape (Circular vs. Elliptical):
- Circular orbits (e.g., Starlink LEO satellites) give consistent coverage and predictable timing which is great for communications.
- Elliptical orbits (e.g., Molniya orbits used by Russia) allow long “dwell times” over high latitudes, useful for regions poorly served by GEO satellites.
- Equatorial Angle (Inclination):
- This is the tilt of the orbit relative to Earth’s equator.
- Equatorial (0°): Good for satellites that want continuous coverage along the equator.
- Polar (90°): Satellites pass over the poles and eventually cover the entire Earth, often used for Earth observation and reconnaissance.
- Inclined orbits: Balance between global coverage and efficiency.
- Direction of Rotation (Prograde vs. Retrograde):
- Prograde (with Earth’s rotation) is most fuel-efficient and commonly used.
- Retrograde (against rotation) is less efficient but sometimes chosen for coverage or security reasons.
From a cyber security perspective, geometry also affects the track surface, for example:
- LEO mega-constellations means more satellites to protect but the risk is distributed.
- GEO satellites are fewer but higher-value targets due to single points of failure.
Frequencies & Bands
SATCOM operates across specific radio frequency bands authorised by the International Telecommunication Union (ITU) and the FCC. The higher frequency bands give access to wider bandwidths but are more susceptible to signal degradation due to rain, snow or ice in the atmosphere
Each band has its own characteristics, trade-offs, and typical applications. One of the key challenges with lower bands is congestion due to the number of satellites in use.
| Band | Frequency Range | Common Uses | Advantages / Limitations |
|---|---|---|---|
| L-band | 1–2 GHz | GPS (GNSS), mobile satphones, IoT devices | Lower frequency - penetrates atmosphere and weather well, but limited bandwidth for data-heavy applications. |
| C-band | 4–8 GHz | Satellite TV, older broadband links | Reliable and less affected by rain fade, but requires larger antennas. |
| X-band | 8–12 GHz | Military communications, weather radar | Reserved largely for government/military → less congestion, but limited spectrum available. |
| Ku-band | 12–18 GHz | Consumer satellite TV, broadband internet | Higher capacity and smaller dishes, but more vulnerable to rain fade. |
| Ka-band | 26–40 GHz | High-throughput broadband (modern satellite internet, e.g., Starlink) | Very high capacity, supports fast internet, but strongly affected by weather conditions (rain fade). |
The Cyber Threat Landscape in SATCOM
Cyber threats to satellite communications are not new. The earliest reported cases date back to the 1980s and 1990s, though many of these were not “cyber” in the modern sense. Instead, they often took the form of radio-frequency interference, such as deliberate jamming or hijacking of broadcast signals. A famous example is the 1986 “Captain Midnight” incident, where a satellite technician overrode HBO’s satellite feed in protest of subscription fees. By the late 1990s, however, attacks had evolved into more direct cyber intrusions, most notably the reported compromise of the U.S-German ROSAT X-Ray satellite in 1998, which was allegedly commanded to position its solar panels directly toward the sun cause permanent damage its sensors.
Over the past two decades, as expected, both attacks and defences in SATCOM have evolved. Traditional attacks have generally focused on disrupting or exploiting the communication link itself. Common examples include:
Jamming: Flooding a frequency with noise to block legitimate satellite signals is known as jamming. Examples include ongoing interference in conflict zones such as Ukraine and the Middle East, and more recently a case where the EU chief’s plane was hit by suspected GPS jamming. While most jamming incidents are temporary disruptions, the worst-case impact is severe: aircraft, ships, and ground forces could lose critical navigation, potentially leading to accidents, operational paralysis, or deliberate misdirection during conflict.
Spoofing: This involves broadcasting false signals, such as fake GPS data to mislead receivers. High-profile incidents in 2017 saw ships in the Black Sea reporting positions hundreds of miles from their true locations. In a worst-case scenario, spoofing could deceive critical infrastructure like ports, energy grids, or autonomous systems, or divert military units into vulnerable positions, creating both safety and strategic risks.
Eavesdropping: This refers to intercepting unencrypted satellite traffic, which was historically common in older SATCOM systems. Researchers have demonstrated that with relatively inexpensive equipment, it was possible to listen in on communications from satellite services. While interception might seem passive compared to jamming or spoofing, its worst-case impact is substantial: sensitive diplomatic, military, or commercial data could be exposed, enabling espionage, intellectual property theft, or manipulation of financial and logistics operations.
Attacks on the ground segment have become one of the most visible examples of how cyber threats to satellites are evolving. A recent example is the Viasat KA-SAT incident in 2022, where attackers exploited ground infrastructure disabling thousands of modems across Europe and disrupted military communications.
Another growing concern is the supply chain. Many modern satellites, particularly smaller commercial models and CubeSats, rely heavily on commercial off-the-shelf (COTS) components. These components are widely available, making them easier for adversaries to study, exploit, or even backdoor before launch. In the worst case, a vulnerability embedded during manufacturing could provide an attacker with a persistent foothold in orbit, something that would be nearly impossible to remediate once the satellite is deployed.
Sensor spoofing and directed energy attacks represent a new class of cyber-physical threats. Research has shown that lasers can be used to spoof star trackers or sun sensors, causing satellites to miscalculate their orientation. At best, this leads to degraded service as antennas drift off-target; at worst, it could result in complete mission failure or even collisions with other satellites if the navigation system is sufficiently compromised. As high-powered lasers and other directed energy systems become more accessible, the likelihood of these attacks being weaponised increases.
Other areas that are likely to contribute to the growing threat landscape for SATCOM include:
- Cloud-based ground station exploits: With services like AWS Ground Station and Azure Orbital, satellite operators increasingly rely on cloud-hosted infrastructure. While cost-effective, this exposes satellites to the same risks as enterprise cloud (misconfiguration, credential theft, API abuse), but with potentially far more severe consequences if adversaries gain control over telemetry or command systems.
- Software-Defined Exploits: Modern satellites often use software-defined radios (SDRs) and reprogrammable payloads for flexibility. This creates new attack surfaces, as vulnerabilities in SDR firmware or software can be exploited to inject malicious code, alter frequency use, or hijack communication links.
- AI-Powered Attacks: Just as AI and machine learning are being deployed to detect anomalies and defend networks, adversaries are beginning to use them to optimise jamming, spoofing, or intrusion techniques. This could lead to highly adaptive and stealthy attacks that evolve faster than traditional defences.
- Quantum Threats: Satellites are long-lived assets, but many still rely on classical cryptography such as RSA or ECC, which will eventually be broken by quantum computers. Adversaries may already be harvesting encrypted traffic now with the intention of decrypting it later (“harvest now, decrypt later”). In parallel, experiments with quantum key distribution (QKD) over satellite links are exploring ways to mitigate this risk.
Current Security Measures and Novel Techniques
To counter the diverse range of threats facing SATCOM, both traditional defences and novel techniques are in play. However, each comes with trade-offs, especially given the limited power, bandwidth, and processing capacity of satellites.
Cryptographic Protection
The most widely deployed security measure in SATCOM today is cryptography. Encryption and authentication protocols protect telemetry, telecommand, and user data links, ensuring that only authorised parties can access or modify communications.
In practice, this involves a mix of symmetric cryptography (fast but requiring secure key distribution) and public-key cryptography (flexible but more computationally intensive). Both approaches are effective, but they face challenges in satellite environments: limited onboard processing power, the difficulty of distributing or updating keys securely, and the fact that many legacy satellites still rely on outdated algorithms, in some cases using keys weaker than 128-bit strength.
Looking ahead, there is a growing concern about the impact of quantum computing. Once sufficiently powerful, quantum computers could break widely used schemes such as RSA and ECC. This is particularly significant for satellites, which often have long operational lifespans and cannot easily be upgraded. To address this, researchers are investigating post-quantum cryptography (PQC) and quantum key distribution (QKD) via satellites. China’s Micius satellite, for example, has already demonstrated QKD over thousands of kilometres, showing the feasibility of quantum-secure links.
More experimental approaches are also emerging, including DNA-based cryptography, which leverages the complexity of biological sequences to create large, hard-to-brute-force key spaces while remaining lightweight enough for use in resource-constrained satellites.
At best, cryptographic protections ensure confidentiality, integrity, and authentication across SATCOM links. At worst, if poorly implemented or reliant on outdated algorithms, they provide only a false sense of security, leaving satellites vulnerable to interception, replay, or brute-force attacks that may compromise entire missions.
Physical Layer Security (PLS)
Physical Layer Security is increasingly being explored as a lightweight alternative or complement to cryptography. Instead of relying solely on mathematical complexity, PLS leverages the inherent characteristics of the wireless channel, such as noise, fading, or directionality to protect communications. This is especially valuable for satellites, which are constrained in power and processing capacity, and for long-lived missions where upgrading crypto may not be possible.
Key PLS techniques include:
Beamforming
By using multiple antennas (multi-input, multi-output or MIMO systems), a satellite can focus its signal into a narrow beam towards the legitimate receiver. This increases the signal-to-noise ratio for the intended user while making the signal much weaker for any unintended listener outside the beam. For example Starlink satellites employ phased array antennas to dynamically steer beams, both improving performance and reducing the risk of eavesdropping.
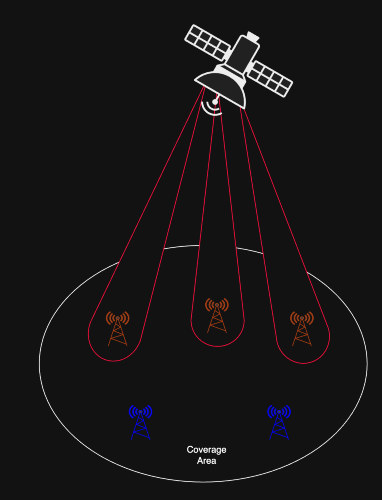
Figure 2 provides an example of beamforming. All ground stations within the satellite’s coverage area can receive signals, but those highlighted in red are within the directed beams and therefore benefit from stronger, more reliable signal strength. Ground stations in blue are outside the main beams and only receive weaker residual signals, making interception or eavesdropping more difficult.
Artificial noise injection
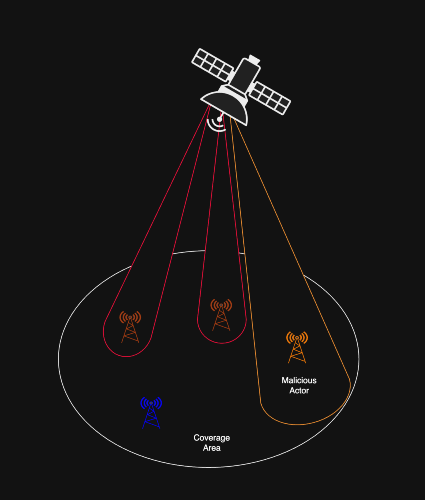
Here, the satellite transmits deliberate “noise” (orange into figure 3) into the channel in directions where eavesdroppers are likely to be located. Legitimate receivers, whose channel characteristics are known, can filter out the noise, but adversaries receive a degraded signal. This approach raises the secrecy capacity of the channel without requiring additional cryptographic processing.
Cooperative Relays
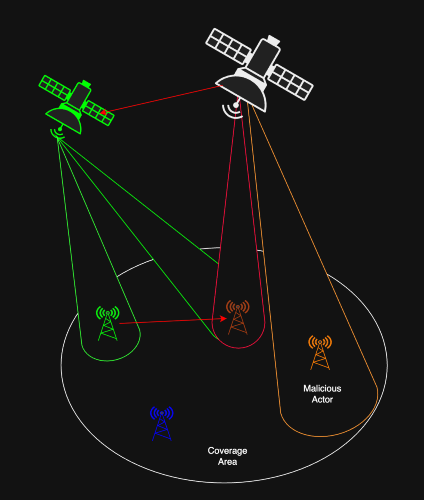
Another promising technique for securing satellite links is the use of cooperative relays. In this approach, additional nodes (green in Figure 4) such as relay satellites, high-altitude platforms, or even ground stations help reinforce communication with legitimate users while simultaneously degrading the channel available to adversaries.
In principle a relay can amplify and forward the intended signal, making it easier for the authorised user to receive, while at the same time introducing interference or noise in the direction of an eavesdropper. This creates an asymmetry: the legitimate user benefits from a stronger, clearer channel, while the malicious actor’s reception is weakened or rendered useless.
Anti-jamming and Anti-spoofing Measures
Because satellites operate in open spectrum, their signals are especially vulnerable to jamming (deliberate interference) and spoofing (false signal injection). These attacks remain among the most common against SATCOM and can have severe consequences for navigation, timing, and communications.
Anti-Jamming
Spread-spectrum techniques
These methods make it harder for an adversary to target a single frequency, forcing them to expend far more power to disrupt/jam communications. Military SATCOM systems have relied on these techniques for decades. Examples include:
- Frequency hopping - The signal rapidly switches between different frequencies in a pseudorandom pattern known only to the transmitter and receiver. This means an attacker has to jam the entire band at once to succeed, which requires far more power and resources. Frequency hopping remains one of the most effective and widely used anti-jamming techniques in both military and commercial systems.
- Direct-sequence spread spectrum (DSSS). Here, the original signal is multiplied by a high-rate pseudorandom code, spreading it over a much wider bandwidth than necessary. To an adversary, the signal looks like background noise and is very hard to isolate or jam. Only receivers with the correct spreading code can de-spread the signal and recover the original transmission. DSSS is a core technique behind GPS and many military SATCOM links.
Adaptive Beamforming
In addition to its role in physical layer security, adaptive beamforming is also a highly effective anti-jamming technique. Here the emphasis is not on minimising signal leakage but on suppressing interference. By dynamically reshaping antenna patterns, satellites can place nulls in the direction of a jammer while keeping strong beams on legitimate users. This makes it far more difficult for adversaries to deny service without expending significant power.
Anti-Spoofing
Navigation Message Authentication
For anti-spoofing, one of the most significant advancements is Navigation Message Authentication (NMA), which is already being deployed in Europe’s Galileo GNSS. NMA works by attaching a cryptographic signature to the navigation data that satellites broadcast, allowing receivers to verify that the information genuinely originates from the satellite and has not been tampered with. In practice, the satellite operator generates the signature using secret keys, and receivers validate it with the corresponding public key. This means that if an attacker attempts to spoof GNSS signals with false positioning data, the receiver can immediately detect the forgery and reject it. While NMA does not prevent all types of attacks, such as jamming or the replay of valid signals, it raises the difficulty of mounting a successful spoofing attack, protecting users against one of the most dangerous SATCOM threats.
Doppler shift analysis
Another technique for detecting spoofed signals is Doppler shift analysis. As satellites orbit the Earth at high speeds, the frequency of their signals experiences a predictable Doppler shift when received on the ground, similar to the change in pitch of a passing siren. Legitimate signals will follow this expected Doppler pattern, which can be calculated in advance based on satellite orbits. Spoofed signals generated from the ground, however, will not exhibit the same frequency shifts. By comparing the measured Doppler shift against the expected values, receivers can identify suspicious transmissions and flag them as potential spoofing attempts. While this approach cannot prevent all spoofing, it provides an additional layer of verification that is especially useful when combined with other methods such as Navigation Message Authentication.
Evolving areas
More recently, research has turned towards the use of AI and machine learning (ML) to strengthen SATCOM security. Traditional defences rely on static rules or predefined thresholds, which can struggle against adaptive or stealthy attacks. In contrast, AI models can be trained to recognise the subtle differences between genuine signals and those that have been altered, injected, or jammed by adversaries. By continuously analysing patterns in real time, these systems provide operators with earlier warnings and a better chance of mitigating attacks before they cause significant disruption.
In practice, AI and ML can support both signal-level anomaly detection (spotting irregularities in waveforms, Doppler shifts, or timing) and network-level intrusion detection (identifying unusual traffic patterns across SATCOM networks). While these approaches are still in the research and early deployment stages, they represent a promising step towards more adaptive and resilient defences in the face of increasingly sophisticated threats.
The Future of SATCOM and Cybersecurity
The role of satellites in global communications is expanding rapidly. With the growth of mega-constellations such as Starlink, OneWeb, and Amazon’s Kuiper, the number of satellites in orbit is set to increase into the tens of thousands. These constellations will form the backbone of future connectivity, extending the internet to the most remote corners of the planet and underpinning next-generation technologies such as 6G and the Internet of Things (IoT). At the same time, satellites are becoming more integrated into critical infrastructure, from navigation and logistics to finance, aviation, and national security.
This evolution brings with it an expanded threat surface. More satellites, more inter-satellite links, and more cloud-connected ground infrastructure mean more opportunities for adversaries to exploit vulnerabilities. Attackers are unlikely to be limited to nation-states; as the technology becomes more commercialised and consumer-facing, criminal groups and non-state actors will see value in targeting SATCOM for disruption, extortion, or espionage.
From a security perspective, the future will require multi-layered defences that combine:
- Lightweight onboard security such as physical-layer techniques (beamforming, artificial noise, cooperative relays).
- Robust cryptography, including post-quantum schemes and potentially quantum key distribution for the most sensitive missions.
- AI-driven anomaly detection capable of responding in real time to adaptive jamming or spoofing.
- Global standards and governance frameworks to ensure that even commercial constellations adopt baseline cybersecurity measures.
Emerging technologies will cut both ways. Artificial intelligence will enhance defences but also enable more adaptive, stealthy attacks. Quantum computing poses a long-term risk to today’s encryption but also inspires new secure communication methods like quantum key distribution. On-orbit servicing and cooperative satellite operations create opportunities for resilience but also introduce new risks of cyber-physical tampering in space.
Ultimately, the future of SATCOM cybersecurity will be defined by how well the industry can balance speed, cost, and security. Satellites are no longer isolated scientific tools they are becoming part of the global digital fabric. Protecting them will mean treating them as such: applying the same rigour we expect in enterprise cybersecurity, while recognising the unique constraints of operating in space.
This is my first exploration into the world of satellite communication and security, and at this stage I know I’ve only scratched the surface. I hope this post has served as a useful introduction for those of you who have read this far. My aim has been to share what I’ve learned so far, while also solidifying my own understanding. I’ll continue to build on this knowledge and I welcome feedback, challenges, and discussion from others working in this space.
Other Resources used that are not linked above: